[NEWS] Intel Develops Hardware-Based Antivirus -> http://goo.gl/4z7mC
[POST] Evil Packaging on OSX with Xcode and Metasploit -> http://goo.gl/sQHy6
[PAPER] Exploitability: 94 pages about exploiting Windows and Linux -> http://goo.gl/6AqRE
[INFO] Chef: systems integration framework -> http://goo.gl/KcS5u
[POST] Smartphone botnet C&C over SMS (Shmoocon 2011 – slides & code) -> http://goo.gl/qw6dK
[POST] An introduction to oclHashcat+ & cudaHashcat+ -> http://goo.gl/LLNot
[INFO] Re2: an efficient, principled regular expression C++ library -> http://goo.gl/5s5zF
[POST] ATM Skimmers That Never Touch the ATM -> http://goo.gl/a46B0
[SCRIPT] pdnstool: queries several passive dns databases -> http://goo.gl/hOZnb
[VIDEO] Exploiting BlogEngine.NET 1.6.x (cloud enhanced exploit) -> http://goo.gl/6N6Fe
[NEWS] Yet another Android Browser exploit that affects the new Android =< 2.3 -> http://goo.gl/4ERNJ
[NEWS] Pod2g Discovers New Untethered Jailbreak Vulnerability -> http://goo.gl/azSxG
[TOOL] NIELD: Network Interface Events Logging Daemon v0.1 released -> http://goo.gl/DbVmq
[SCRIPT] Knock v1.4.4: enumerate subdomains on a target domain through a wordlist -> http://goo.gl/5GLil
[PAPER] Antivirus Firewall Evasion Techniques Evolution of Download Deploy Shellcode (PDF) -> http://goo.gl/V7tzA
[PAPER] Effectiveness of Antivirus in Detecting Web Application Backdoors (PDF) -> http://goo.gl/FC084
[TOOL] Mausezahn v0.40: free and fast traffic generator -> http://goo.gl/qlgwh
[TOOL] Java Cisco Group Password Decrypter -> http://goo.gl/WebjA
[PAPER] Vulnerability discloses PIN used in Microsoft Excel secure printing (PDF) -> http://goo.gl/fjLlW
[NEWS] Stop Cross-Site Scripting Errors Now: Veracode Launches Free Detection Service -> http://goo.gl/1HJ5K
[VIDEO] Ubertooth One: an open source Bluetooth test tool -> http://goo.gl/fsR4e
[POST] How Does Cross-Site Scripting Become Arbitrary Code Execution? An Ode to the Oft-Maligned Referer Header -> http://goo.gl/jWZJn
[POST] The Cases of the Blue Screens: Finding Clues in a Crash Dump and on the Web -> http://goo.gl/64iBn
[ADVISORY] Cisco WebEx .atp and .wrf Overflow Vulnerabilities -> http://goo.gl/vFJb2
Monthly Archives: January 2011
Geek quote of the day – 2011.01.31
I failed the Turing test
An introduction to oclHashcat+ & cudaHashcat+ (by d3ad0ne via ob-security.info)
Introduction:
Lets face it, when it comes to passwords humans are predictable. Time and time again we see this when a site gets compromised. After the hashes have been sorted the top password are nearly always the same. It’s usually some variation of 1-9, password, iloveyou, princess, abc123, qwerty, 111111, secret, etc. Many of these passwords are unoriginal, and people use these same passwords across all of their accounts. Then their are the individuals that think they are being unique, and will change one of these common passwords to something slightly different for example [password –> Password123]. A dictionary tool with a rule engine can easily find these types of passwords. Up until now all these dictionary based/ rule engine tools have mostly CPU based (hashcat & JTR for example). Using a dictionary with 14 million passwords and a rule file with only 3000 rules could take as long as 15 – 20 minutes with a CPU based tool. That same 14 million password wordlist can take about 2 hours using my custom 23k rule set(preloaded in the /rules folder). This is where oclHashcat+/cudaHashcat+ come in.
Application:
oclHashcat+/cudaHashcat+ which I will call “oclHashcat+” for the sake of simplicity in this article is a completely new tool, separate from regular oclHashcat. oclHashcat+ is a dictionary based tool with a full featured rule engine that all run completely on the GPU. In our above example a 23k rule file combined with a 14 million word dictionary would take about 2 hours running on a modern CPU at about 50M password attempts /sec. With oclHashcat+ this same same rule set and dictionary file takes as little as 3.5 minutes using a dual GTX 480 system running at about 2B password attempts /sec. That’s right folks 50M for the CPU vs 2000M on the GPU. But that’s not all, oclHashcat+ offers us a couple of new features which I’ll be going over here.
The first thing to point out is that there are now four separate .bin/.exe files. This is to cover the various different system combinations that people may be running. The switches and syntax for all of these different versions are the same, however depending on your GPU, OS and OS architecture your running will depend on which one you’ll be using. For example someone with Ubuntu 64 running a Nvidia card would use cudaHashcat+64.bin while someone running a Windows 32 bit system with an ATI card would run oclHashcat+32.exe. I find the easiest way to get rid of the clutter in your folder is to delete those extra .bin/.exe files. Since I’m running Ubuntu with nvidia cards I delete all the exe files, and ocl prefixed bin files. Just in case your complete baffled by this here is a simple cross reference table:
| Windows system | Linux system | |
|---|---|---|
| ATI w/ 32bit OS | oclHashcat+32.exe | oclHashcat+32.bin |
| ATI w/ 64bit OS | oclHashcat+64.exe | oclHashcat+64.bin |
| nVidia w/ 32bit OS | cudaHashcat+32.exe | cudaHashcat+32.bin |
| nVidia w/ 64bit OS | cudaHashcat+64.exe | cudaHashcat+64.bin |
The only exception being that 64bit OS’s can run the 32bit versions (oh though I don’t know why you’d want to). The reason for the forking of the project into separate CUDA and OCL variations comes from a programming standpoint, certain optimizations can only be done using vendor specific code. This gives us a nice performance increase because the code is better optimized to support that architecture.
Features:
oclHashcat+ uses a lot of similar switches and syntax as the other Hashcat tools. The attack mode numbers such as 0 for MD5, 1000 for NTLM, 1100 for DCC are all the same. If you run the –help switch it will list all the various switches.
- One thing you may notice is that a few more attack modes are supported now that have only been supported on the CPU version. The attack modes -m 400 covers MD5(wordpress and phpBB3) and -m 500 covers MD5(unix). These algorithms are generally difficult hash types to attack due to the high iteration counts that a plaintext goes through while getting hashed. High iteration algorithms may reduce the overall attacking speed of a hash but it doesn’t do anything to protect those passwords that users always tend to use, even if those passwords are only slightly different from the norm.
- Support for standard in – For those that have already built special scripts or have various other ways to mangle or generate wordlist this is a way to continue to use those. In addition since oclHashcat+ doesn’t support bruteforce style attacks directly you can use the maskprocessor from hashcat-utilities to generate a bruteforce character set and pipe it to stdin.
- GPU based rule engine – oclHashcat+ supports nearly all of the same rules that hashcat supports except for the @ modifier. That means any of the rule list you may have built before to use in Hashcat will also work. You can also generate random rules using the -g switch. -g 1000 would generate 1000 random rules.
Usage & Conclusion:
Here is an example usage and output:
./cudaHashcat+64.bin -r rules/d3ad0ne_23.8K.rule -n160 -o found.out example0.hash /root/dict/rockyou.txt
...
...
Rules: 22656
Platform: NVidia compatible platform found
Device #1: GeForce GTX 480, 1535MB, 1520Mhz, 15MCU
Device #2: GeForce GTX 480, 1535MB, 1520Mhz, 15MCU
Device #1: Kernel ./kernels/4318/m0000.sm_20.64.cubin
Device #2: Kernel ./kernels/4318/m0000.sm_20.64.cubin
Starting attack in wordlist_mode...
p: 553/6494, cs: 1, cr: 1920, cl: 8, rt: 1546.73ms, s:1627030.75k/s
p: 657/6494, cs: 1, cr: 3968, cl: 8, rt: 1200.40ms, s:2096458.25k/s
p: 708/6494, cs: 1, cr: 6016, cl: 8, rt: 1214.36ms, s:2072357.88k/s
p: 740/6494, cs: 1, cr: 8064, cl: 8, rt: 1224.98ms, s:2054383.12k/s
Here we can see that I used the -r switch to specify a rule file, I set the workload to 160 using -n, saved the found hashes in the found.out file using the -o, example0.hash is our hashlist and rockyou.txt is the dictionary file. One thing to note you may have seen a lot of “Skipping invalid or unsupported rule in line ###” This is typical, as oclHashcat+ does not support all of the same rules as regular hashcat. It simply skips the rules but will use all the ones that it does support.
The status output means the following – p:progress, cs:current salt, cr:current rule, cl:current (plain) length, rt:runtime, s:speed.
Something to keep in mind is that for non iterated hashes such as md5, ntlm, md4 you need to keep the GPU constantly busy. That is to say that if you were to try to crack MD5 with no rules using a standard dictionary oclHashcat+ speeds would be very low, this is because the GPU can calculate the MD5 sum of a dictionary word much faster than that word can be sent through the bus to the GPU to be processed. That’s why it’s suggested to use at least several hundred rules. The rules act like iterations, constatly keeping the GPU busy.
oclHashcat+ can be downloaded here
hashcat-utillites can be downloaded here
Check back soon as I’ll cover some helpful tips and techniques.
Original post: http://ob-security.info/?p=211
4li3n’s after midnight useless news and links – 2011.01.31 (*Shmoocon* edition)
Just a few links this time mainly because all researchers are at Shmoocon 2011!
[DISCLOSURE] More on Microsoft Internet Explorer MHTML Protocol Handler XSS -> http://goo.gl/AOfh1
[POST] Mac OS Forensics How-To: Simple RAM Acquisition and Analysis with Mac Memory Reader (Part 1) -> http://goo.gl/fckpV
[NEWS] More on Sourceforge.net attack -> http://goo.gl/mwXpP , http://goo.gl/1UXLt
[TOOL] Farebot: Read data from MIFARE public transit cards using your NFC-equipped Android phone -> http://goo.gl/AEnkW
[NEWS] Former Kaspersky Employee Responsible for Leaked Source Code -> http://goo.gl/YOdpf
[SCRIPT] pyOLEScanner 1.3: detect Malicious Office Files -> http://goo.gl/am9dG
[INFO] Carberp Trojan Removes Antivirus Scanners, Other Malware from Host -> http://goo.gl/cCYi6
[INFO] Exclusive interview with Linus Torvalds -> http://goo.gl/41xjq
[PAPER] Plug and Prey: Malicious USB Devices (Shmoocon 2011) -> http://goo.gl/mzmIm
[NEWS] Shmoocon 2011: Overview -> http://goo.gl/NpVJL
[NEWS] Shmoocon 2011: Printer to Pwnd -> http://goo.gl/WE43F
[NEWS] Shmoocon 2011: Printers gone wild! -> http://goo.gl/C34ep
[NEWS] Shmoocon 2011: TEAM JOCH vs. Android – The Ultimate Showdown -> http://goo.gl/DfLmj
[NEWS] Shmoocon 2011: Attacking 3G and 4G mobile telecommunications networks -> http://goo.gl/mbEUn
[NEWS] Shmoocon 2011: Defeating mTANs for profit -> http://goo.gl/eEu17
[NEWS] Shmoocon 2011: URL Enlargement – Is it for you? -> http://goo.gl/h2itx
Geek quote of the day – 2011.01.30
> SELECT * FROM users WHERE clue > 0
0 rows returned
Shmoocon 2011: Printers gone wild! (by Ben Smith via c22.cc)
Printers are everywhere… they are ubiquitous!
Everybody seems to ignore them. They get plugged in, and just work!
HP Basics
Listens on tcp/9100
Admin page on 80/443
Many have hard disks!
HP printers have 3 passwords
- Web admin
- Telnet (same as the wedadmin)
- PJLPassword
PJLPassword can be used to lockout the console, make disks read-only etc…
PJLPassword is weak… no brute-force protections
PJL is unathenticated and widely supported, going away, but will be here for a while.
SNMP can be disabled through the Web Admin, however encoding them specially they will still answer SNMP requests over port 9100
Google search “PJL DMINFO ASCIIHEX” for more info
Overview
PJL (Printer Job Langauge)
Sets up printer for jobs
Created by HP, used in many other devices
Really old!
Fun PJL commands
- FSUPLOAD (not an upload)
- FSDOWNLOAD (not a download)
- FSDIRLIST
- FSDELETE
- RDYMESSAGE
- DMINFO ASCIIHEX
There’s een lots of research before (Hijetter etc…)
Bringing that into the modern environment with printFS
printFS
Python tool for covert file systems using HP printers
Distributes files over multiple printers
Uses the printer RAM disks or physical disks
Works on any supported printer via network or the internet!
All stored files are compressed/encrypted and saved using random filenames
All files are stored twice with different names and keys to improve redundancy (files in RAM disk are lost on restart)
Supports panic mode (panic) remotely reboots every device in the file table to destroy the data
pfsScanner
multithreaded scanner
Scans printers to see if necessary commands are supported to use printFS
Scans are randomized in the order that functions are run and the timing between them
Test upload files are random data and given random names
Entire scan peppered with random sleeps
pyPJL
Main support lib
Used by all tools
Implements most of the documented PJL commands
printJack
A support tool for doing nasty funny things
User interface to the PJL password cracker
Mass control panel lock/unlock
Mass RamDisk/Disk Lock/Unlock
Pass printing (toner is cheap!)
pyPJLpass
Support class for printjack
Brute-forces all possible password combinations in about 2 hours (single thread)
So now it’s threaded to check multiple printers… all communicate together until one valid password is found (password reuse)
Other fun stuff to do to PJL
- Mass reboot loop
- Mass connect to port 9100 and remain connected (blocking)
- Animated LCD messages
- SE LCD messages (please call xxxxx)
- Mass disk lock
- Mass printing
- Mass control panel locking
Limitations
Can only upload files form the directory you are running printFS from
Known issue where some printers won’t respond to pfsScanner if they’re offline
To ensure that printers can still print when being scanned, dynamic class is used (generating huge traffic)
Code Release
Remote-exploit.org will receive it within the next week
Links:
Original post: http://blog.c22.cc/2011/01/29/shmoocon-2011-printers-gone-wild/
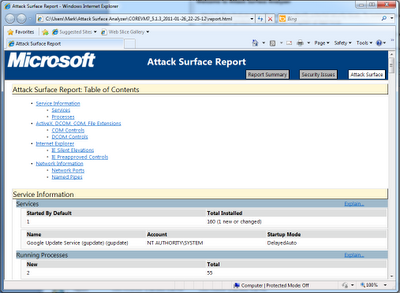
Microsoft Attack Surface Analyzer – Review (by Mark Linton for TripleCheckConsulting)
- Directories With Weak ACLs – related to the use of NT SERVICETrustedInstaller (needs more investigation to see why this was reported)p.p1 { margin: 5px 0px; font: 12px ‘Times New Roman’; }
- Processes With NX Disabled – GoogleCrashHandler.exe included in the software does not use DEP security options (why not?)
- Services Vulnerable To Tampering – The Google Update service that was installed is also susceptible to tampering by the NT SERVICETrustedInstaller account.
- New Service – Google Update Service
- New Running Processes – google crash handler and a .NET framework utility
- 113 New Registered COM Controls – IE mostly but controls used within the software.
- 3 New Internet Explorer Silent Elevation Entries / Preapproved controls – Google Update plugin – This is interesting as it looks like this gets added to the list of approved protected mode controls – more investigation needed here.
- 1 New TCP Port – Established outbound TCP port on 49336. This is likely the port used by the google update service and checks for updates during the install. Not sure more investigation likely here as well.
- 6 New Named Pipes
Geek quote of the day – 2011.01.29
An IPv4 address space walks into a bar: “A strong CIDR, please. I’m exhausted.”
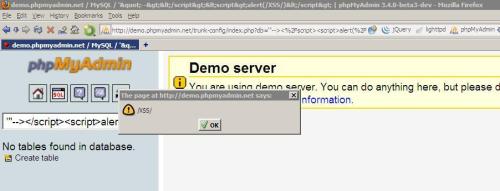
phpMyAdmin 3.4.x, 3.4.0 beta 2 <= Stored XSS Vulnerability (by YGN Ethical Hacker Group via vul.kr)
===================================================================================
phpMyAdmin 3.4.x, 3.4.0 beta 2 <= Stored Cross Site Scripting (XSS)
Vulnerability
===================================================================================
1. OVERVIEW
The phpMyAdmin web application 3.4.0 beta 2 and lower versions of
3.4.x were vulnerable to Cross Site Scripting.
2. PRODUCT DESCRIPTION
phpMyAdmin is a free software tool written in PHP intended to handle
the administration of MySQL over the World Wide Web.
phpMyAdmin supports a wide range of operations with MySQL.
The most frequently used operations are supported by the user
interface (managing databases, tables, fields, relations,
indexes, users, permissions, etc), while you still have the ability to
directly execute any SQL statement.
3. VULNERABILITY DESCRIPTION
The ‘db’ parameter in phpMyAdmin was not sanitized and an attacker can
inject XSS string in ‘db’ field when creating or renaming a database.
An attacker can create new database name or rename database name
through several means like SQL Injection in user’s vulnerable web
applications or
compromise of user account through brute-force or bypassing CSRF protection.
Even though the phpMyAdmin uses httpOnly as a protection against
cookie theft via XSS, attacker could use XSS tunneling proxy to
manipulate database names and fields. From it, he could execute
arbitrary database commands to allow him higher access to the server.
4. VERSIONS AFFECTED
phpMyAdmin 3.4.0 beta 2 and lower versions of 3.4.x
Vendor confirmed this flaw did not exist before the 3.4 version family.
Thus, it is assumed 2.x and 3.3 <= versions are not affected.
5. PROOF-OF-CONCEPT/EXPLOIT
http://demo.phpmyadmin.net/trunk-config/index.php?db=%27%22–%3E%3C%2Fsc…
6. IMPACT
Attackers can compromise currently logged-in user session, plant xss
backdoors and inject arbitrary SQL statements
(CREATE,INSERT,UPDATE,DELETE)
via crafted XSS payloads.
7. SOLUTION
For those who’re using version phpMyAdmin 3.4.0 beta 2 and lower,
check out the latest commit (git pull).
8. VENDOR
phpMyAdmin (http://www.phpmyadmin.net)
9. CREDIT
This vulnerability was discovered by Aung Khant, http://yehg.net, YGN
Ethical Hacker Group, Myanmar.
10. DISCLOSURE TIME-LINE
2011-01-26: notified vendor
2011-01-26: vendor released fix
2011-01-27: vulnerability disclosed
11. REFERENCES
Vendor Commit: http://phpmyadmin.git.sourceforge.net/git/gitweb.cgi?p=phpmyadmin/phpmyadmin;a=commit;h=f57daa0a59a0058a4b3be1bbdf1577b59d7d697a
Original Advisory URL:
http://yehg.net/lab/pr0js/advisories/phpmyadmin/[phpmyadmin-3.4.0-beta2]_cross_site_scripting(XSS)
CWE-79: http://cwe.mitre.org/data/definitions/79.html
Previous Releases:
http://www.phpmyadmin.net/home_page/security/PMASA-2010-6.php
http://www.phpmyadmin.net/home_page/security/PMASA-2010-5.php
http://www.phpmyadmin.net/home_page/security/PMASA-2008-5.php
http://www.phpmyadmin.net/home_page/security/PMASA-2008-6.php
#yehg [2011-01-27]
———————————
Best regards,
YGN Ethical Hacker Group
Yangon, Myanmar
Our Lab | http://yehg.net/lab
Our Directory | http://yehg.net/hwd
_______________________________________________
Full-Disclosure – We believe in it.
Charter: http://lists.grok.org.uk/full-disclosure-charter.html
Hosted and sponsored by Secunia – http://secunia.com/
Original post: http://www1.vul.kr/phpmyadmin-3-4-x-3-4-0-beta-2
4li3n’s after midnight useless news and links – 2011.01.29 (*back-in-business* edition)
[PAPER] Attacking Oracle Web Applications with Metasploit (PDF) -> http://goo.gl/R4YJP
[UPDATE] L0phtCrack v6.0.11 available -> http://goo.gl/8cYpl
[DISTRO] Debian GNU/Linux 5.0.8 released -> http://goo.gl/cGmDB
[INFO] Option to force SSL on all traffic on Facebook, but not yet -> http://goo.gl/UaxoN
[POST] Wireshark SMB capture feature for Windows -> http://goo.gl/ijwl6
[INFO] API Monitor Tutorial: Using Breakpoints to modify application output -> http://goo.gl/BkjoA
[INFO] Regular Expressions with Windows PowerShell -> http://goo.gl/cEIep
[INFO] Facebook photo exploit allows you to view any albums of non-friends -> http://goo.gl/aRzkY
[EXPLOIT] Stored XSS Vulnerability in phpMyAdmin 3.4.x, 3.4.0 beta 2 -> http://goo.gl/Nzeix
[TOOL] PyChecker: Python Code Analysis -> http://goo.gl/qYXmb
[ADVISORY] SQL Injection in RunCMS -> http://goo.gl/fb/WlIbM
[ADVISORY] Path disclosure in RunCMS -> http://goo.gl/fb/aqcdu
[ADVISORY] XSS vulnerability in RunCMS -> http://goo.gl/fb/3kr0D
[POST] Mark Zuckerberg’s Facebook Fan Page Hacked -> http://goo.gl/y8Lx0
[INFO] PHP Nuke site still infected -> http://goo.gl/91vZd
[EXPLOIT] XSS in www.facebook.com (fixed) -> http://goo.gl/aiks7
[EXPLOIT] XSS in m.facebook.com (unfixed) -> http://goo.gl/xBYJd
[NEWS] Hackers turn back the clock with Telnet attacks -> http://goo.gl/zXPm9
[INFO] Firewall/IDS Evasion and Spoofing with Nmap -> http://goo.gl/4KLvR
[POST] EXT3 File Recovery via Indirect Blocks -> http://goo.gl/gaB76
[NEWS] Sourceforge Attacked and several servers were Compromised -> http://goo.gl/ZJ0z3
[TOOL] Gdbinit v0.1 for iOS (iPad at least :-)) -> http://goo.gl/GoYsm
[WTF!] Windows XP Patch: Snow White & the Seven Dwarves DVD Issue -> http://goo.gl/6Af6j
[VIDEO] Interesting virtual machine escape hacking demo video from NSA -> http://goo.gl/bpM7U
[INFO] MS Attack Surface Analyser review -> http://goo.gl/tx9OP
[NEWS] Happy New Year Geohot – Court Orders Seizure Of PS3 Hacker’s Computers -> http://goo.gl/SgYdL
[EXPLOIT] FreeBSD 8.0 Local Denial of Service (forced reboot) -> http://goo.gl/UehsF
[TOOL] PacketFence v.2.0.1 Released -> http://goo.gl/fb/0S7oQ
[INFO] How to analyze a malicious PDF file using JSunpack-n on REMnux -> http://goo.gl/2OXFP
[UPDATE] The Social-Engineer Toolkit v1.2 “Shakawkaw” Released -> http://goo.gl/lnIjy
[POST] LOIC DDoS Analysis and Detection -> http://goo.gl/XJiif
[VIDEO] Android 2.2 bug exploited with Metasploit/XSSF -> http://goo.gl/OzqWh
[UPDATE] Nmap 5.50 released -> http://goo.gl/7gtjG , http://goo.gl/PGBlY
[POST] Amazon.com Security Flaw Accepts Passwords That Are Close, But Not Exact -> http://goo.gl/qyR2E
[0DAY] Zero day vulnerability found in Windows MHTML renderer -> http://goo.gl/cG3vt